(Wordpress version here. As an FYI, I am now composing all posts in Wordpress, and simply copying them over here.)
Norse Technologies, one of the leading network-security and monitoring companies, has released an absolutely mesmerizing global map that shows, in real time, global hack attempts, including the type of hack, the origin of the hack, and the intended target. That's a picture of it in the header, and while writing this post I also was fortunate enough to witness a massive, coordinated attack that you can see in the image below. Fun!
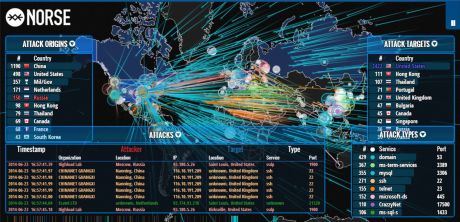
You
can hover over any on-screen element top get more information about
that particular attempt. Norse achieves all this by using its own honeypot
infrastructure. A honeypot is a type of server that sits between the
Internet and a company network, and is intended to look like a regular
server on said network. However, it is actually specifically designed to
attract hack attempts and fool the attacker into thinking they have
successfully gained access to a system or network, all the while while
monitoring the attempt and gathering as much information as it can in
order to learn about network vulnerabilities or to gather information
for a potential prosecution. Honeypot servers can be deployed in several
ways, however it is not uncommon for them to have a small amount of
actual corporate data on them to maintain the ruse for as long as is
required.
They also mention they are following darknet
attacks, but I don't know why that would be necessary. Darknets are
networks that run underneath the Internet, using virtual private
networks and tunneling protocols and things of that nature to avoid
detection and access (Silk Road,
in the news a lot recently, was a darknet used to traffic weapons,
drugs, in some cases even people), but there are enough regular attacks
that darknet monitoring wouldn't be necessary. I suspect their use of
the term is representative of their own network of honeypot servers.
NOTE: I could only get the site to run smoothly in the Chrome browser, and it's worth downloading just for this. It worked in Internet Explorer and Firefox after a refresh, but very slowly, so be aware.
.jpg)
No comments:
Post a Comment